Your Questions About Passwordless Authentication Answered
Published: Dec 5, 2022

The importance of data security and protecting your accounts cannot be understated. The potential for identity theft, credential theft, stuffing, data breaches, and other malicious activities is a real and ever-present danger in our increasingly connected world. Hackers can replace your passwords and lock you out of your account indefinitely.
Using a password alone isn’t enough to protect your accounts anymore, but choosing to implement passwordless authentication can provide you with that security.
What is Passwordless Authentication?
Passwordless authentication is a verification method that, as the name implies, does not require a user to enter a password. This can be accomplished using a variety of techniques, such as sending a one-time code to the user's mobile phone or email or using biometric authentication factors like a fingerprint or face scan.
This method of user authentication is more secure than the traditional one because it eliminates the risk of password reuse and phishing. It is also better for the user experience, meaning people no longer need to remember multiple passwords.

The Importance of Passwordless Security
In this day and age, digital information is more ubiquitous and abundant than ever before. And the more data out there, the higher the security risk. Password-based methods of accessing devices and applications have been around for quite a while. Not only are they vulnerable to data breaches, however, but they’re also redundant; imagine having to type in a long, complex passcode each time you want to log in.
This creates the need for a more reliable passwordless authentication method that guarantees security while being as convenient as possible. In an information-driven world, passwordless login ensures that access to valuable information is easy for users but almost impossible for hackers.
The Evolution of Authentication
Traditional Password-Based Authentication
Traditionally, the process of authenticating our digital identity involved typing in our usernames and passwords. It’s the technique we all know and, in certain cases, still use to this day. The system sends a query to a user directory, either on a server or on a local operating system. If the credentials happen to match, the system grants access to the user.
The Limitations of Password-Based Authentication
Despite being a common form of an authentication factor, passwords are also among the most vulnerable. And it’s quite easy to see why, considering how many people use this method. Many people often use the same password for several different websites and applications, making it considerably easier for hackers to gain access to all the accounts after managing to hack into one. And this is just one of the problems with password authentication.
The Shift Towards Passwordless Methods of Authentication
With the shortcomings of password-based authentication proving to be too problematic, more and more businesses are adopting a passwordless authentication solution. These include a variety of robust and innovative methods like facial recognition and fingerprint scanning. Passwordless authentication has already become widespread among industries like healthcare and financial services, where digital information is considerably sensitive and the risks of cyber attacks are always looming.
Text Message API Service Pricing
Dexatel employs a pay-as-you-go approach that charges you per sent message. This is the most affordable SMS gateway pricing model, and the service costs are free of setup, monthly, or any other fees.
Types of Passwordless Authentication Factors
Hardware Security Tokens
A hardware security token is a physical device used to authenticate a user's identity. The most common types are smart cards, USB tokens, and one-time password tokens. Smart cards are small, portable, and durable. They can be used for a variety of applications, including physical access control, logical access control, and identity management. USB tokens share similar features. OTP tokens are the least popular type of hardware security token. They are large, bulky, and difficult to carry.
Certificate-Based Authentication
Certificate-based is a form of passwordless authentication factor that uses a document called a public-key certificate to verify users. This can be a major advantage for users, as it eliminates the risk of forgetting a password and being locked out of the system.
When a user attempts to log in to a system, the latter checks to see if the user has a valid certificate. If they don't, the system won't allow the user to log in.
OTP Email
OTP email passwordless authentication is a standard method that can be used to protect account logins. It involves sending a unique code via email to the user's email address, which the user can then enter on the login page to authenticate their account.
This passwordless authentication factor eliminates the need for users to remember complex passwords. It also makes it much more difficult for hackers to gain access to accounts, as they would need to compromise both the user's email account and the OTP code to log in. However, hackers can intercept the OTP code if they have access to the user's email account.
Email Magic Links
Email magic links are an innovative new way to authenticate without the need for a password. They can be sent directly to the user's email address.
These links provide a much simpler process that's less likely to result in frustration or abandoned accounts. Even if someone manages to intercept the link, they would still need to have access to the user's email account to log in.
Authenticator Apps
Authenticator apps use either a time-based one-time password (TOTP), a universal two-factor (U2F), or multi-factor authentication (MFA) to generate a code to log in to an account.
With TOTP, a code is generated based on the current time and a secret that is shared between the app and the service you’re logging in to. The code is only valid for a short period of time. U2F uses a physical security key that must be inserted into a USB port or NFC reader to generate the code.
Fingerprint Scan
Fingerprint scanning is a form of biometric authentication that uses an individual's fingerprint as a password. When used for authentication, a fingerprint scanner captures an image, which is then compared to a database of known fingerprints. If the fingerprint matches one in the database, the user's device is authenticated and granted access.
Facial Recognition
Facial recognition works by scanning the user's face and comparing it to a stored database of images. If the user's face matches one of the images in the database, then they are verified and can access their account. Passwords can be guessed from lost or stolen credentials, but it is much harder to replicate someone's face.
Voiceprint
Voiceprint authentication is a method of verifying a user's identity by their voice. This passwordless authentication works by recording a person's voice, then using algorithms to extract unique characteristics from the recording. These characteristics are then used to create a template, which can be used to verify the person's identity.
Voiceprint authentication can be used in conjunction with other forms of identification, such as fingerprint or retinal scanning.
SMS
SMS is also very convenient for passwordless access. Users can simply enter their phone number to log in, and they will receive an SMS message with a one-time code to complete the login process.
There are a few advantages to using text messaging as a form of passwordless authentication. It's convenient, secure, reasonably priced, and available worldwide.

Is Passwordless Login Safe?
Passwordless authentication methods pose a great obstacle for those trying to gain unauthorized access to accounts and sensitive information. These methods are significantly more difficult to crack than conventional passcodes and are highly immune to most cyber attacks. Be that as it may, no form of authentication is 100% safe. Sophisticated hackers with advanced tools will often find clever, less obvious ways to work around certain defenses. Of course, this is much less likely to happen with passwordless systems than with password-based ones.
What Are The Benefits of Passwordless Login?
Authentication without passwords reinforces the element of security by getting rid of questionable password management methods and minimizing attack vectors. Moreover, it enhances the user experience by taking away the frustration that comes with trying to remember passwords and security questions.
Passwordless authentication eliminates the need for users to remember and enter lengthy and complex passwords.
One of the most common ways that hackers gain access to accounts is through phishing attacks. But this method reduces the risk of password reuse and phishing attacks, as well as the opportunity for hackers to guess or brute force their way into a user's private key or accounts.
Moreover, passwordless login can be faster and more efficient than traditional password-based authentication methods.
At the end of the day, other authentication methods without a password can give you greater peace of mind. They offer greater convenience and usability, making them an attractive option for organizations looking to improve their authentication process.

Passwordless Security Solutions
Okta
As a leader in the identity and access management industry, Okta provides passwordless authentication through email links, biometrics, smartcards, factor sequencing, SSO (single sign-on), and security keys. The company offers a flexible and scalable platform that supports over 7,000 integrations with applications both on-premise and in the cloud. In addition to the Okta Verify app, key features of Okta’s solution include in-depth reporting capabilities, centralized user management, and mobile device management.
Microsoft Azure AD
With 425 million users worldwide, Microsoft’s Azure Active Directory (Azure AD) is a leading identity and access management solution. The software offers a range of features like SSO, multi-factor authentication (MFA), and passwordless authentication options. Praised for being scalable, reliable, and easy to use, Azure AD is ideal for companies and organizations across every industry. It is especially suitable for enterprises that want to benefit from passwordless security.
Dexatel
As a business messaging platform provider, Dexatel provides a form of passwordless login as part of its features. Brands can configure a passwordless connection to send a one-time password (OTP) to a user through SMS to complete the authentication process. This prevents the user from having to enter their credentials every time they need to sign in. Instead, an OTP is sent to the user’s phone number, and the user can then log in with the code. If the code is not used within a certain timeframe, it will expire, and the user will need to request a new one. This adds another layer of security to the entire process.
OneLogin
OneLogin’s identity and access management platform provides a plethora of products with various capabilities. These include SSO, SmartFactor Authentication, and an advanced directory. Users can enable passwordless authentication through MFA, SSO, and certificate-based trust. MFA methods of passwordless access include SMS authentication, email, biometrics, and the company’s own OneLogin Protect authenticator app. The platform is available in 25 different languages, making it ideal for businesses that have a global presence.
AuthO
AuthO offers a passwordless experience through its premium security features that businesses can use for their web applications. Users can authenticate via one-time passcodes through an SMS text or magic links through email. The solution also features a built-in attack prevention mechanism that immediately blocks the IP addresses of hackers and notifies you on the spot. AuthO’s comprehensive services include MFA, SSO, universal login, account linking, and log retention.
Yubico
Yubico combines security with the convenience of a simple login process. It does so by offering YubiKey, a portable hardware key that you can use to access networks, devices, applications, and web-based services. In addition to being fast, reliable, and user-friendly, this crush and water-resistant piece of hardware doesn’t need any batteries or a network connection to work. Companies and organizations can use the YubiKey for secure passwordless authentication by simply inserting it into a computer and touching the sensor, or by tapping it on the back of a mobile device (to trigger NFC).
How To Use Passwordless Authentication With Dexatel's API
The Dexatel SMS API allows the use of passwordless auth with OTP SMS. You need to connect your application or website to the Dexatel Platform using the Dexatel Verify API.
The purpose of the Verify API is to generate and send a one-time code to a user's phone number. This way, users can enter the code sent to their phone numbers to log in to their accounts.
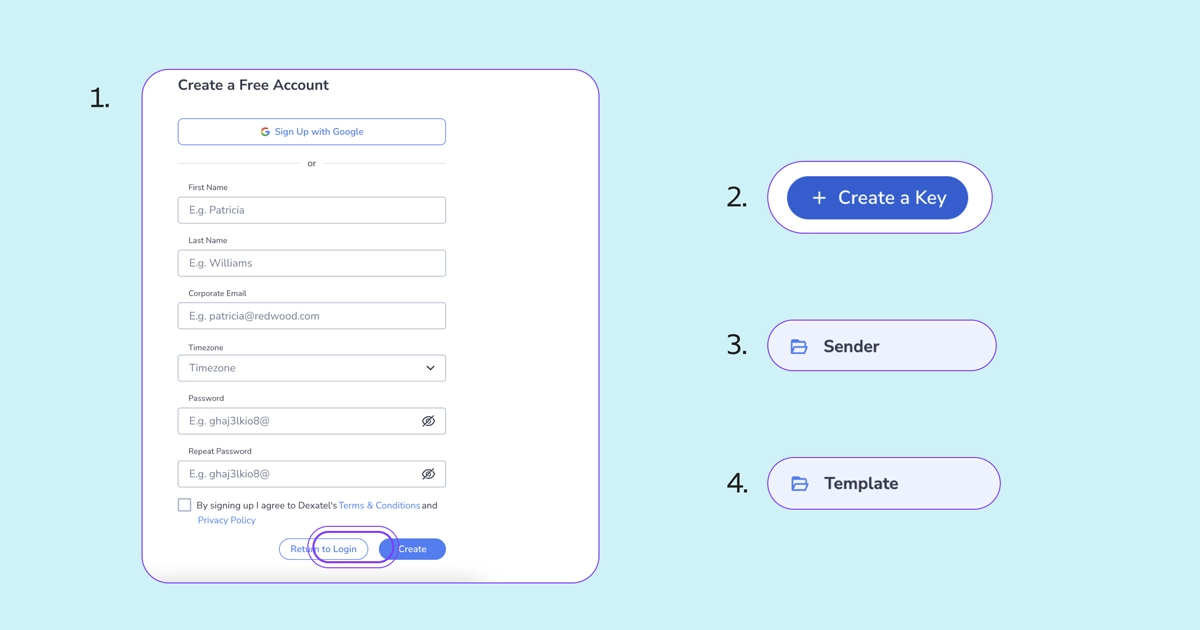
1. Create an Account
Create a free account on the Dexatel CPaaS platform. Log in to your dashboard and manage your account settings, like topping up your account, updating information, and more.
2. Generate a Unique API Key
Then, go to the API Keys section, where the system will generate a unique API key. You will then use that as a credential to send automatic requests on your behalf.
3. Create a Sender Name
To do this, you can add your brand name to the Sender IDs in the dashboard. But another way to go about this is by sending a POST request to the Sender endpoint. This will allow you to send OTP messages with a customized ID.
4. Get a Template ID
Then, go to the Templates page or send a POST request to the Template endpoint. Once a template is created, the API will generate a template ID for you to use. To get your template ID, send a POST or GET request to the Template endpoint.
When creating a template text, feel free to use any character depending on the destination country. However, you must include a {code} variable in it. The Dexatel Verify API will generate a random OTP and replace it in your message instead of {code}.
Here are a few verification templates to set up:
Your code is {code}. Do not provide it to anyone.
Your verification code is {code}. Complete it as soon as possible.
Your registration code is {code}. Thank you!
5. Ask for Your Clients’ Phone Numbers
Once everything is set up, ask your customers to provide their phone numbers for logging in to your account and make sure to verify them.
For future attempts, you can request a code from the Dexatel Verify API to create and send to your customers’ phone numbers. Once a recipient enters the correct code, they will be able to log in to the platform without any static password.
